How Crypto Address Poisoning Scams Operate Without Compromising Private Keys
Scammers use address poisoning to flood victims' transaction records with fraudulent entries, leading unsuspecting users to mistakenly transfer cryptocurrency to attacker-controlled wallets.

Key takeaways
- Address poisoning targets user habits rather than cryptographic security. Scammers insert fake addresses into transaction histories and depend on victims inadvertently selecting a fraudulent lookalike address.
- Real-world incidents such as the 50-million-USDT theft in 2025 and the 3.5 wBTC compromise in February 2026 show how straightforward interface manipulation can result in devastating financial consequences.
- Features like copy buttons, visible transaction records and unrestricted dust transfers make fraudulent addresses seem legitimate within wallet user interfaces.
- The permissionless nature of blockchain technology allows anyone to transfer tokens to any wallet address. Most wallets display every transaction, including unsolicited spam, creating opportunities for attackers to insert malicious entries.
The majority of cryptocurrency holders assume their digital assets remain safe so long as their private keys stay confidential. Yet, as an increasing number of fraud cases demonstrate, this assumption doesn't always hold true. Criminals have been deploying a particularly devious method, known as address poisoning, to pilfer assets without ever gaining access to a victim's private key.
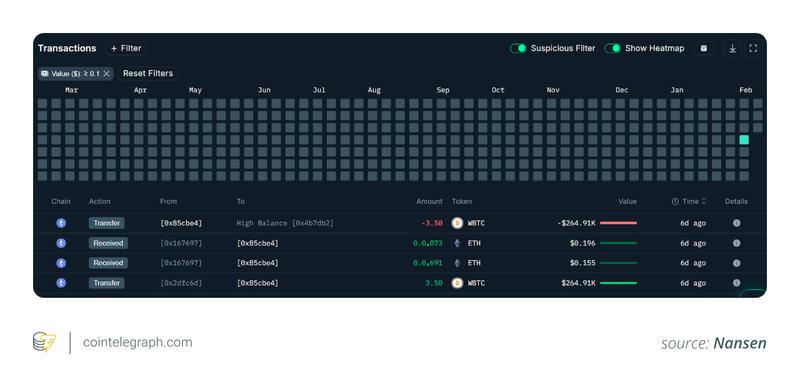
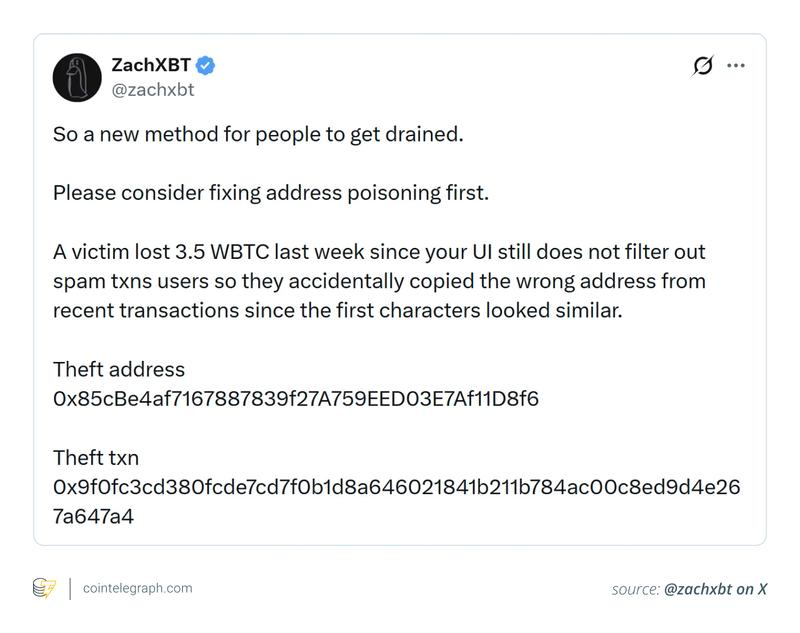
During February 2026, a phishing operation exploited a Phantom Chat functionality. Through an address poisoning technique, the perpetrators managed to siphon approximately 3.5 Wrapped Bitcoin (wBTC), valued at over $264,000.
During 2025, one victim suffered a loss of $50 million in Tether's USDt (USDT) following the copying of a compromised address. These types of events have emphasized how inadequate interface architecture and commonplace user behaviors can lead to catastrophic financial damage.
Well-known cryptocurrency personalities such as Binance co-founder Changpeng "CZ" Zhao have openly called on wallet providers to implement more robust protective measures in response to address poisoning attacks.
This piece examines how address poisoning schemes leverage user conduct instead of compromising private keys. It outlines the methods attackers use to tamper with transaction records, explains why this strategy proves successful on transparent blockchain networks and identifies practical measures both users and wallet creators can implement to minimize exposure.
Understanding the mechanics of address poisoning
In contrast to conventional cyberattacks that focus on compromising private keys or exploiting software vulnerabilities, address poisoning works by contaminating a user's transaction record to trick them into transferring assets to an incorrect destination.
Typically, the attack unfolds through the following sequence:
- Fraudsters locate high-value wallets using publicly accessible blockchain information.
- They generate a wallet address that bears a strong resemblance to one the target frequently interacts with. For instance, the attacker might replicate the initial and final several characters.
- They transmit a minimal or zero-value transaction to the target's wallet from this counterfeit address.
- They count on the target duplicating the attacker's address from their recent transaction history at a later time.
- They receive the assets when the target inadvertently pastes and transmits them to the fraudulent address.
The target's wallet and private keys are never compromised, and blockchain encryption remains intact. The scam succeeds entirely through human mistakes and reliance on recognizable patterns.
Did you know? Address poisoning attacks experienced a significant increase coinciding with the emergence of Ethereum layer-2 solutions, where reduced transaction costs enable attackers to economically send dust transactions to tens of thousands of wallets simultaneously.
Methods attackers employ to create misleading addresses
Cryptocurrency addresses consist of extended hexadecimal character sequences, frequently comprising 42 characters on Ethereum-compatible blockchain networks. Wallet applications typically display only an abbreviated format, like "0x85c...4b7," which criminals exploit. Fraudulent addresses possess matching initial and final segments, while the central portion varies.
Legitimate address (example format):
0x742d35Cc6634C0532925a3b844Bc454e4438f44e
Poisoned lookalike address:
0x742d35Cc6634C0532925a3b844Bc454e4438f4Ae
Criminals utilize vanity address generation tools to produce these nearly identical character strings. The counterfeit address shows up in the target's transaction log due to the dusting transfer. For users, it appears legitimate upon casual inspection, particularly because they seldom confirm the complete address sequence.
Did you know? Certain blockchain exploration platforms now automatically flag questionable dusting transactions, assisting users in identifying potential poisoning efforts before engaging with their transaction records.
The reasons behind this scam's remarkable success rate
Multiple interconnected elements contribute to making address poisoning remarkably efficient:
- Human constraints when processing lengthy character sequences: Since addresses lack user-friendly formatting, people depend on rapid visual verification of the first and last portions. Criminals take advantage of this behavioral pattern.
- User-friendly yet dangerous wallet capabilities: Numerous wallets provide convenient copy functions adjacent to recent transactions. Although this feature proves useful for authentic purposes, it introduces danger when fraudulent entries infiltrate the list. Researchers like ZachXBT have identified instances where victims duplicated poisoned addresses straight from their wallet interface.
3. Technical exploits unnecessary: Given that blockchains operate as public and permissionless systems, any party can transmit tokens to any destination. Wallet software generally shows all received transactions, spam included, and users commonly place confidence in their own transaction records.
The weakness exists in human behavior and user experience design, not in cryptographic methods or key protection.
The limitations of key security as sole protection
Private keys manage authorization, which means they guarantee that only you possess the ability to authenticate transactions. Nevertheless, they offer no confirmation regarding whether the recipient address is accurate. Blockchain's fundamental characteristics — unrestricted access, transaction finality and minimized trust requirements — result in malicious transactions becoming permanently documented.
Throughout these fraudulent schemes, the user voluntarily approves the transfer. The infrastructure operates precisely as intended, and the weakness exists in human decision-making.
Fundamental psychological and architectural challenges include:
- Habitual patterns: Individuals frequently transfer funds to identical addresses repeatedly, leading them to duplicate from their transaction records rather than manually inputting addresses.
- Mental fatigue: Transactions require multiple considerations, including addresses, transaction costs, network selections and confirmations. Numerous users consider examining every character burdensome.
- Abbreviated displays: Wallet interfaces conceal the majority of the address, resulting in incomplete verification.
Did you know? Under certain circumstances, attackers streamline address lookalike creation using GPU-accelerated vanity generation tools, enabling them to create thousands of nearly matching wallet addresses in mere minutes.
Effective strategies to enhance security
Although address poisoning takes advantage of user conduct rather than technological weaknesses, minor adjustments in transaction practices can substantially diminish the threat. Grasping several practical protective strategies can assist cryptocurrency users in preventing expensive errors without needing sophisticated technical expertise.
For users
Straightforward confirmation practices and transaction discipline can considerably lower your probability of becoming a victim of address poisoning fraud.
- Create and maintain a confirmed address registry or approved list for regular recipients.
- Confirm the complete address. Utilize a verification tool or examine it character by character prior to executing payments.
- Avoid copying addresses from recent transaction records. Rather, manually enter addresses or employ saved bookmarks.
- Disregard or flag unexpected small transfers as likely poisoning tactics.
For wallet developers
Careful interface architecture and integrated protective features can reduce user mistakes and render address poisoning attacks considerably less successful.
- Screening or concealing minimal-value spam transactions
- Resemblance identification for destination addresses
- Transaction preview simulations and hazard alerts
- Integrated poisoned address verification through onchain queries or collaborative blacklists.